In the specialized domain of system memory analysis and anti-cheat evasion, the concept of “2PC-Cross LeechCore” has emerged as a topic of technical discussion. This methodology represents a specific adaptation of established Direct Memory Access DMA techniques, shifting the paradigm from hardware-based to network-based memory interaction.
This analysis provides a detailed, objective deconstruction of its core technology, architectural implementation, inherent security posture, and the practical realities of its operational model.
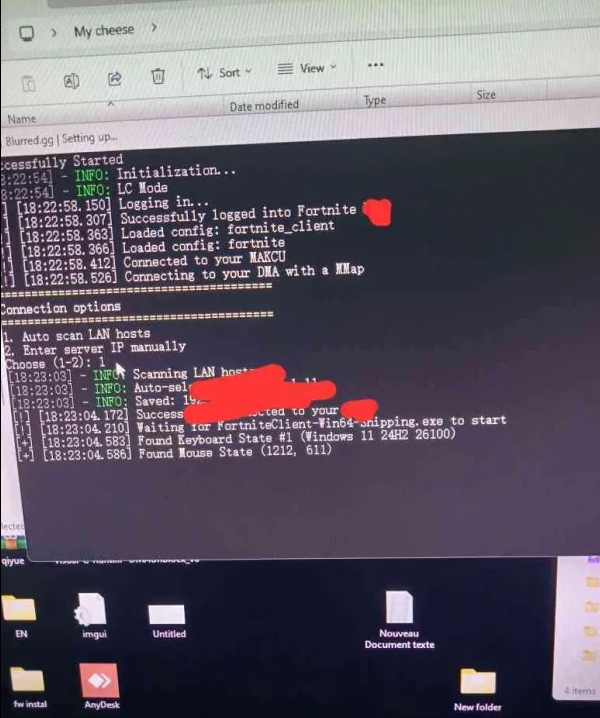
Core Technical Architecture: From DMA to RMA
Fundamentally, this tool is an implementation of a Remote Memory Access (RMA) framework. It is a significant modification of the open-source LeechCore library, which is traditionally coupled with FPGA hardware (like the PCILeech project) to perform physical DMA reads from a target system.
The architectural innovation—or more accurately, the re-application of a classic systems programming concept—lies in its client-server model over TCP/IP:
- Target-Side Agent (“Server”): A software component, often a repurposed or modified physical memory acquisition driver (e.g., a derivative of WinPmem or a custom kernel module), executes on the primary system. Its sole function is to read the physical memory space of the host.
- Network Abstraction Layer: Raw memory data is packetized and transmitted over a standard local network connection.
- Client-Side Analysis Engine: On a secondary, physically separate machine, a modified LeechCore client receives this network stream. It presents a compatible interface that emulates a local DMA hardware device. Consequently, any analysis or manipulation software—such as memory scanners or game cheat clients designed for DMA hardware—can operate transparently on this remote memory stream.
This design achieves a key objective: the complete separation of the monitoring/analysis tools from the target system’s execution environment. No specialized PCIe hardware is required in the target machine, and the potentially detectable analysis logic resides entirely on an external computer.
Exploitation Vector: The Vulnerability Conduit
A critical and revealing aspect of common public implementations is their reliance on User Account Control (UAC) bypass and known software vulnerabilities for privilege escalation, rather than a custom, robust driver.
Analysis of distributed packages has identified the exploitation of CVE-2021-40212, a local privilege escalation vulnerability in specific builds of the PotPlayer media application.
The operational chain is as follows:
- The tool requires the installation of a vulnerable version of PotPlayer (e.g., 64-bit version 1.7.21523).
- It leverages this application’s flaw—an out-of-bounds write (CWE-787)—to execute arbitrary code with elevated SYSTEM privileges.
- From this privileged context, it can load its memory-reading components or directly manipulate system memory.
This dependency on a patched, public CVE is a significant weakness, making the toolchain inherently fragile and detectable by modern endpoint security solutions that monitor for exploitation of known vulnerabilities.
Operational Model and Security Implications
The tool is typically distributed under a tiered, software-as-a-service model:
- “Public/Pro” Tier: Marketed for circumventing mainstream anti-cheat services. It often relies on the aforementioned vulnerable-application exploit chain, leading to a higher risk of rapid, signature-based detection.
- “Private” Tier: Purportedly uses more advanced, stealthier techniques such as custom—and sometimes fraudulently signed—kernel drivers or hypervisor-based isolation to conceal its activities. This tier claims compatibility with more aggressive anti-cheat systems utilizing HVCI (Hypervisor-protected Code Integrity).
Critical security implications for any user of such a tool include:
- Botnet and Backdoor Risk: The requirement to install software that exploits kernel-level privileges on the target PC presents an extreme threat. The operator of the tool has unfettered control over the system.
- Inevitable Detection: The network traffic pattern of streaming full memory contents, coupled with the exploitation of known CVEs or the detection of unusual kernel drivers, creates multiple detection vectors. Anti-cheat systems can blacklist the vulnerable host application, detect the memory-read driver, or identify the network behavior.
- Commercial Exploitation: The subscription model and claims of exclusivity are classic markers of commercial exploitation within this niche, often overstating the novelty and longevity of the technique to less-informed buyers.
2PC-Cross LeechCore Historical Context and Technical Assessment
Labeling this as “new technology” is a misnomer. The core principle—accessing one machine’s memory from another over a network for debugging or analysis—is a foundational technique in low-level systems engineering and reverse engineering, with documented use cases spanning decades.
Modern tools like WinDbg with KDNET utilize this same remote debugging philosophy for legitimate purposes.
2PC-Cross LeechCore Conclusion
The “2PC-Cross LeechCore” concept is a technically coherent but operationally risky application of remote memory access principles. Its innovation is not in the core idea, which is well-established, but in its packaging and specific adaptation for a particular niche.
Its effectiveness is intrinsically limited by its attack vectors (reliance on old CVEs), its detectable network and system footprints, and the aggressive evolution of anti-cheat solutions designed to identify precisely these patterns of unauthorized memory interaction. For the security practitioner or systems analyst, it serves as a pertinent case study in how old techniques are continuously repurposed, and how commercial incentives often outpace the underlying technology’s stealth or novelty.
Want To Get Started With DMA Cheats?
Click Here to Join our exclusive Discord community to get started cheating in your favorite video games!
- COMMUNITY: Connect with fellow DMA gamers and find teammates
- UPDATES: Be the first to know about new updates and features
- SUPPORT: Get personal help and tips directly from me
